TRUSTLESS.AI was closed in October 2023
TRUSTLESS.AI was a Geneva-based startup that was spun off in 2019 from the Trustless Computing Association to build the system, supply chain architecture, proof-of-concept of an hardware and software endpoint platform and ecosystem - compliant to the Trustless Computing Certification Body - for sensitive non-classified and diplomatic communications (Seevik Net) and for control subsystems for critical AIs, and other society-critical subsystems, like mainstream social media feeds (Seevik Controls).
The platform included a server-side endpoint platform, a multinational cloud, as well as a 2mm-thin client mobile device, carried in custom leather wallets or "encased" in the back of top-end Android phones, aimed at far outcompeting the iPhone Lockdown Mode in security & convenience.
It was turned into a "spin-in" of the Trustless Computing Association in 2021. As such, it was bound to be owned by its Trustless Computing Certification Body, with its planned globally-representative participatory intergovernmental governance, in a spin-in group architecture similar to that of the OpenAI.
Seevik Net
Seevik Net aims to far outcompete even the iPhone Lockdown Mode and the best commercially available “cryptophones” in security, convenience and accountability - as will certified by a uniquely-trustworthy Trustless Computing Certification Body according to the Trustless Computing Paradigms.
Seevik Net will include a multi-national private cloud, apps for mainstream mobile app stores, and an ultra-secure 2mm-thin mobile device, the Seevik Pod, carried in custom leather wallets or embedded in the back top-end Android or Harmony smartphones.
While being a stand-alone personal computing device - with Wifi, BlueTooth and NFC connectivity - Seevik devices seamlessly connect to the users' smartphones for Internet connection, data transfers, and bi-directional HW multi-factor authentication.
Seevik Net: a Global Democratic Digital Sphere
The TCCB will guarantee both radically-unprecedented levels of confidentiality and integrity and democratic control as well as national and international legitimate lawful access, by applying the Trustless Computing Paradigms, new win-win IT security paradigms based on uncompromising transparency, time-tested oversight and democratic governance models, extreme security-review in relation to complexity, and multi-national battle-tested open-source technologies.
Through its unique security, privacy, accountability, international democratic control - and mandatory interoperability of TCCB-compliant IT systems and publicly-available apps running on the Seevik devices, Seevik Net will concurrently maximize personal freedoms, democratic control, national security and public safety.
This will turn it into the 1st global democratic digital sphere for human communication and networking, to foster shared truths, fair, secure and efficient dialogue and structural coordination within and among all nations - promote and protect democracy, freedom and security in social democratic and liberal democracies.
Seevik Controls
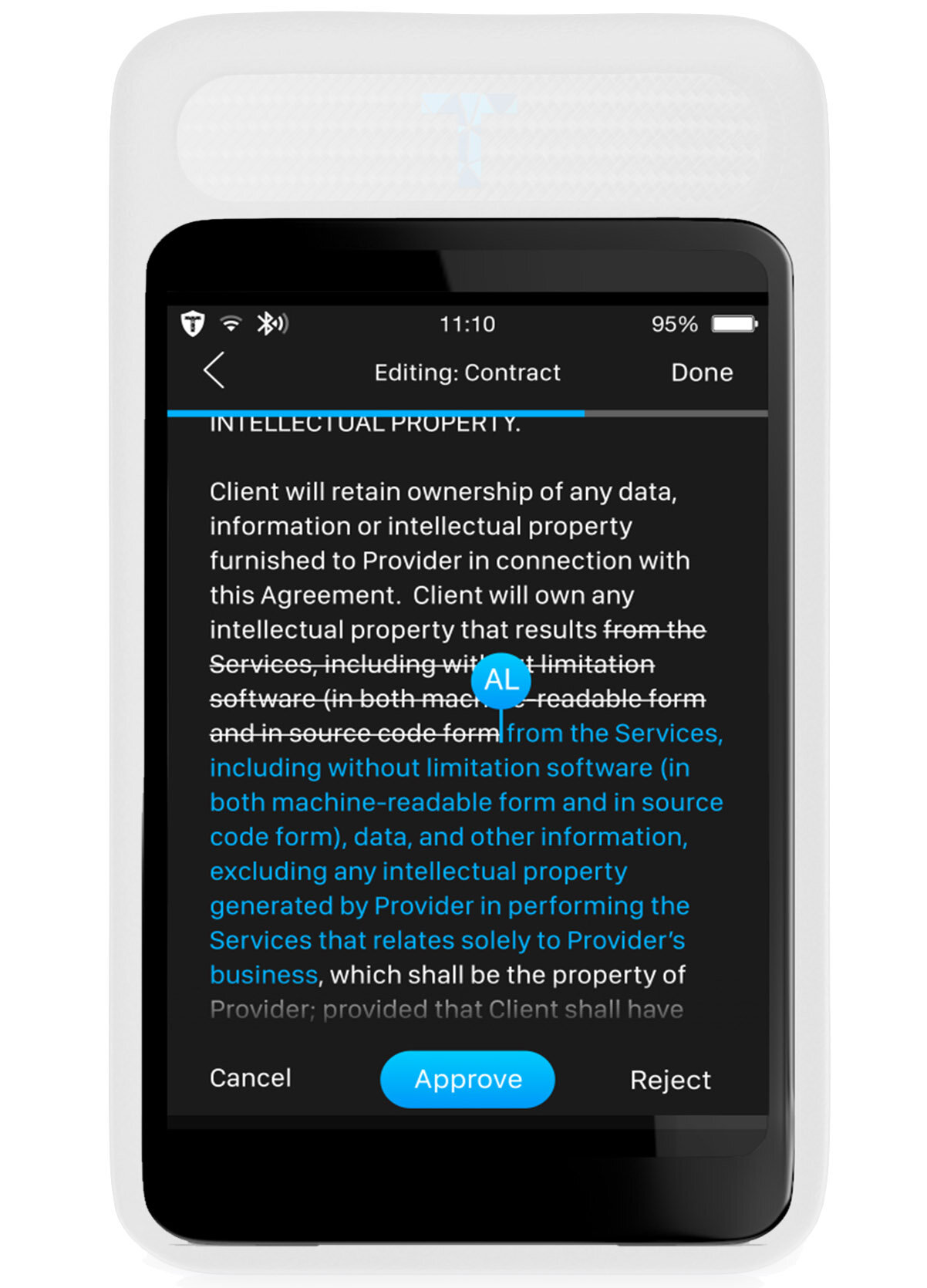
Currently, minimalistic ultra-secure technical and socio-technical systems and standards, called high-assurance, are utilized to ensure the highest levels of security, safety and accountability of the most critical IT systems devoted to functions of control of critical systems that are inherently complex and obscure, such as core “black box” systems of Frontier AIs.
The accelerating power of such platforms and the increasing consequences of potential malicious or accidental failure in security, safety or accountability, makes it imperative that ultra high-assurance systems and standards are developed and conceived with much higher resitance to such failure.
Key to it is to ensure higher transparency of technical designs and processes, more expert and varied security reviews in relation to complexity, trustworthy procedural legitimate lawful access mechanisms, and most importantly higher global participation and neutrality in the standardization and certification governance processes.
Here is a System and Supply Chain Diagram for a Generic AI System for sensitive client-server domains, such as in sensitive medical, financial or personal use:
Unique Security, Privacy and Convenience
We achieve radically unprecedented levels of confidentiality and integrity for one single and simple reason: Seevik Net with its Seevik Cloud and Seevik Pod client device (in its Seevik Wallet and Seevik Phone modes) will be certified, with limited-time exclusivity, as compliant to the Trustless Computing Paradigms, as defined and verified by a new uniquely neutral, competent, accountable and resilient intergovernmental IT security certification and governance body, the Trustless Computing Certification Body (TCCB), which was established last July 2021 in Geneva.
Compliance with TCCB includes the uncompromising application of four socio-technical principles, none of which are adhered to by any of our competitors:
Uncompromising Transparency.
Transparency of the source designs of all hardware, software, and processes, that are critically involved in the entire life cycle.Uniquely extreme Security-Review in relation to Complexity.
Extreme levels of security review in relation to complexity, in the system, life-cycle, and supply-chain, by “incentive-aligned” deep experts.Uniquely extreme Technical and Organizational Oversight.
Citizen-witness and citizen-jury oversight, applied down to hosting rooms access (TCCB Cloud) and chip foundry (TCCB Fab).Uniquely trustworthy Certifications & Paradigms.
Certified by a uniquely democratic, competent, independent, and resilient certification body, based on time-tested socio-technical principles.
The TCCB certification ensures that a given end-2-end IT service ensures both radically unprecedented levels of confidentiality and integrity AND in-person legitimate lawful access by applying to both the same extreme, transparent and battle-tested technical and organisational safeguards, derived from nuclear safety and electoral process engineering.
Far outcompeting the iPhone Lockdown Mode in both security and convenience?
Following reports of mass-scale hacking of iPhones in recent years, last July 2022 Apple introduced the iPhone Lockdown Mode, that enables them to reboot their device in a more secure mode, albeit sacrificing some functionality. In comparison to that ours Seevik Phone offers both much higher security and much higher convenience:
(1) much higher security, primarily because our 2mm-thin device, and its private cloud, will (A) uniquely ensure transparency of the source designs and “extreme security review in relation to complexity” for all IT and processes critically-involve in the entire lifecyle, including for procedural, “in-person” legitimate lawful access mechanism; and (B) will comply to the Trustless Computing Paradigms, as certified by a new neutral, competent, participatory and inter-governmental Trustless Computing Certification Body, established last June 2021 in Geneva.
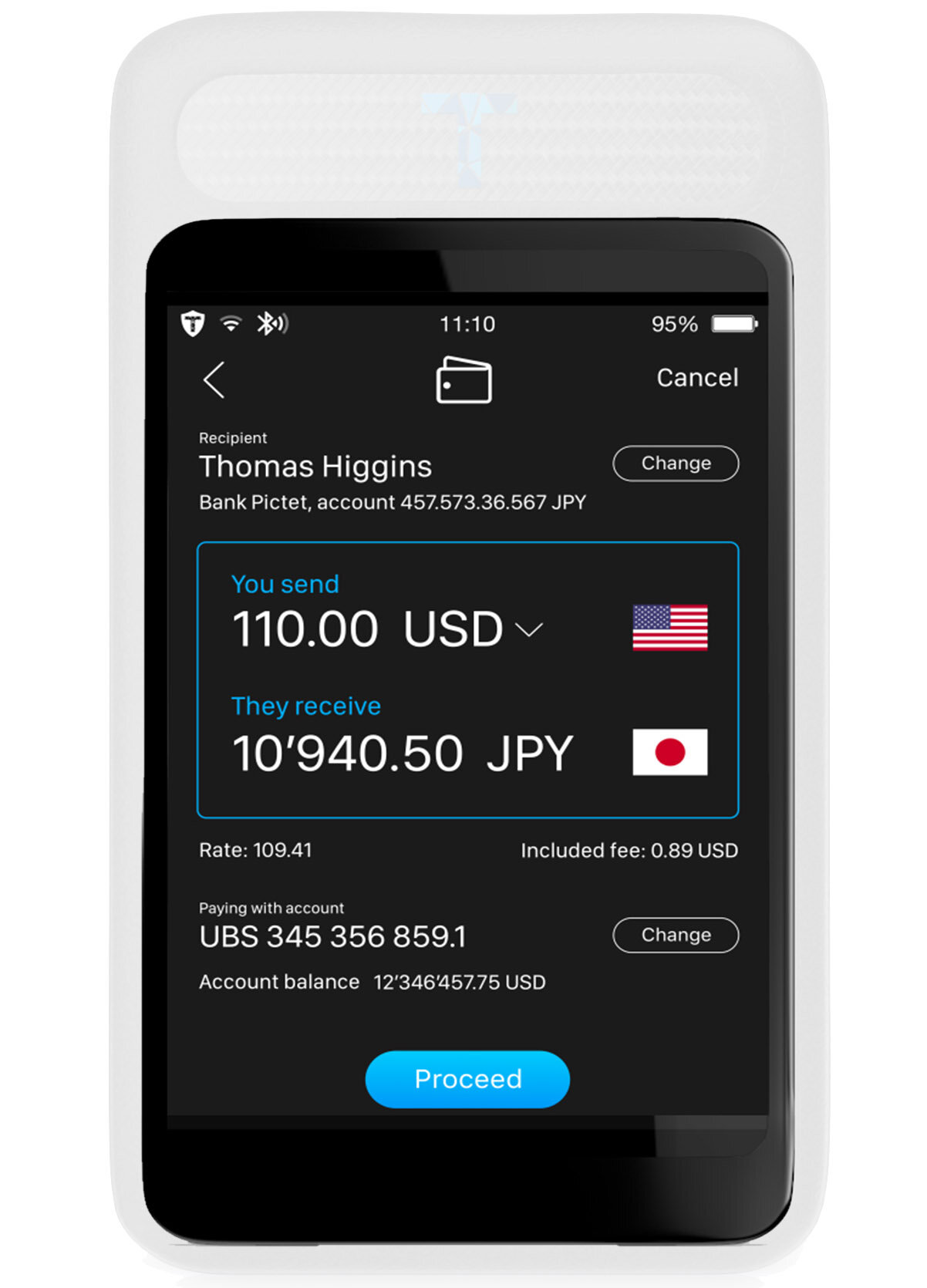
(2) much higher convenience, because the user can switch between secure and less secure mode just by flipping the phone, instead of having to reboot it. To maintain the same security levels, the users’ associates will either purchase a Seevik Phone, or opt to buy a standalone version of the Seevik Pod carried in a custom stylish leather wallet, or Seevik Wallet.
Though the Android part of the Seevik Phone may well be equally or somewhat less secure than the iPhone (unless it is a Samsung Knox), and may even be manufactured in China (like most iPhones still are anyhow), that would be a minor issue for such sensitive users because they'd delegate nearly all their sensitive computing to the Seevik Pod.
Later, simpler Seevik Wallet and Seevik Phone models will be marketed at cost, with only basic default software, to bring digital freedom and democracy to all, becoming the human computing platform of everyone’s private digital life.
Seevik Net: Size of the Problem
Even prime ministers and opposition leaders, and their close associates are illegally, undetectably and continuously hacked on their personal smartphones, as shown in Spain, in Greece, in Finland, in the UK, and in Switzerland, last year alone. And that's just the hacks both discovered and disclosed by the victims!
The problem is much wider, but hard to approximate. NSO Group, just one of a dozen spyware firms in Israel alone, declared last June to the EU Parliament that 13,000 citizens per year are hacked via their Pegasus system.
If that sounds like a high number, that’s just the tip of the iceberg. Consider that such number does not include (1) dozens of other similar spyware companies that rent or sell to many dozens nations and private groups; (2) state security agencies of powerful nations hacking large-scale targeted hacking automation tools; and (3) worse of all, hundreds of entities to discover, buy, steal, or just rent hacking capability, as a “collateral damage” of surreptitious way in which powerful nations ensure their "backdoor" access.
Furthermore, a vast majority of these cyber crimes go undiscovered for years, if ever, as they often leave no trace When discovered, they are nearly always kept secret as both victims and attackers gain from keeping them unreported. Victims are not required to disclose, and the hacking of top officials is very often classified as a state secret.
The most targeted know by now. Pre-covid surveys by UBS and by Northern Trust show that even the 0.2% richest worldwide and family offices regard cybersecurity as their n.2 or their n.1 concern, respectively. If there is such a high demand from the wealthiest and most powerful, why is there no supply?
The root source of this paradox is that all IT and standards are hyper-complex and systematically weakened by security agencies to prevent criminal and enemy abuse of encrypted communications. Liberty and democracy lay dead on the ground as collateral damage of governments efforts to counter adversary nations and terrorism, because They have not yet found a way to reconcile personal freedom and public safety, via win-win solutions, as we did before in communications systems of the pre-digital era.
Seevik Phone
Initially, the Seevik Pod will be available as a premium service for the most targeted persons, in a limited batch of 10,000 units, and carried inside a custom stylish leather wallet in a variety of styles, the Seevik Wallet, with a few default apps and dozens of 3rd party apps, also certified by the TCCB.
Shortly after, we’ll offer the Seevik Phone - in joint venture and co-branding with a premium Android brand or manufacturer - whereby our 2mm-thin standalone Seevik Pod is embedded in the back of a flagship 6 mm-thin Android smartphones.
The translucent and refractive casing that connects the two standalone devices that constitute the Seevik Phone opens an opportunity of astounding lighting effects through day and room lights, as well as through high-efficiency led lights that can be customized by the user’s to match their style or mood, or connected notifications, music, to switching to secure modes.

Unique as we all are!
Every Seevik Wallet and Seevik Phone will be unique in its design, as each one of us is unique. Via our online 3d personalization engine, and design consultants, you’ll be able make it personal, from basic initials engraving to anything you can imagine.
We want our clients to celebrate in their physical World the unimagined digital freedom and control that the Wallet provides to them in their digital world, by customizing its design to reflect the unique being.
Selected as one of the five finalists to the European Cybersecurity Startup of the Year competition of 2020 PwC Cybersecurity Days in Luxembourg.
Selected as one of the five finalists early-stage startups for the 2020 Swiss Fintech Awards, the most prestigious award of its kind in Switzerland.
Selected among hundreds, we graduated for the Q1 2022 program of MACH37, the first and leading US cybersecurity accelerator in the US, located in Virginia.
Mission and Vision 2030
Our mission and vision is to build an inter-governmental organization that will certify and govern IT systems that will realize the incredible positive potential of IT and AI, and stave off ensuing catastrophes and dystopia, by ensuring that they foster fair and effective global dialogue and coordination, and become tools under our control to boost our personal security, happiness, health and abundance.
We are seeking to turn IT and AI into tools under our firm personal and collective control - to boost our freedom, health, wellbeing, wisdom, and wealth and to foster fair and effective global dialogue and global structural cooperation - in order to stave off ensuing catastrophes and dystopia, and realize the promises of the Digital Age.
In time, Seevik Pod and will become the trust hub for sensitive user's’ wearables, VR/AR headsets, workstations; and it’ll help turn advanced AI into a phenomenal tool firmly in our control to greatly increase well-being, health, wisdom, wealth and social life.
About Us
We aggregate co-founders and team aggregate over 50 years of entrepreneurship, cybersecurity, and secure hardware manufacturing. Our advisors and partners even more. Our investors include five highly qualified angel investors from Germany, Luxembourg, London, and Switzerland.
According to a signed spin-in agreement, TRUSTLESS.AI is bound to be owned and controlled by the Trustless Computing Association (to be renamed Trustless Computing Certification Body), via an option to buy 100% of its shares at precisely-set non-speculative conditions with a market standard ROI for external investors and much less for funders.
This unique model enable us to leverage private sector innovation while ensuring a highly democratic and multi-national long-term control of such a sensitive transnational democratic infrastructure.